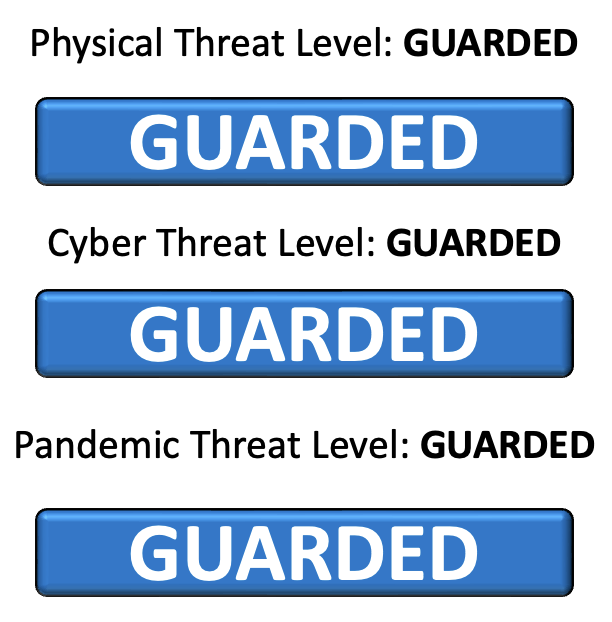
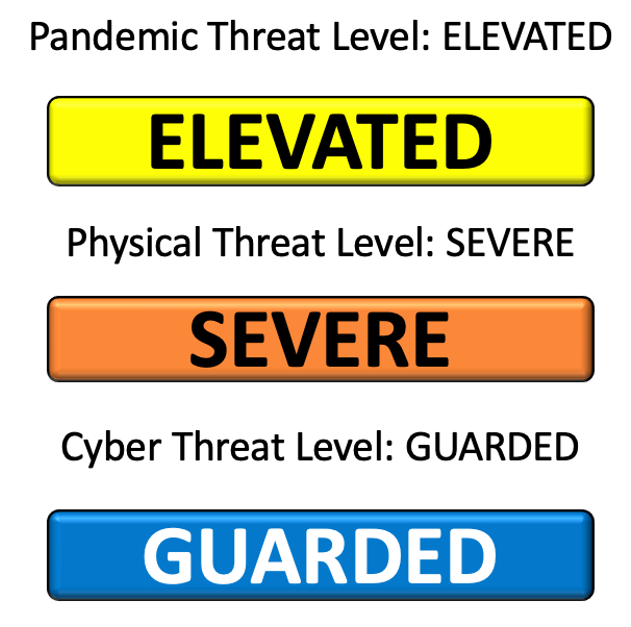
FB-ISAO Threat Level, December 2022 Update
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The FB-ISAO Cyber Threat Intelligence, Operational Resilience (together, the Threat and Incident Response) working groups have been actively monitoring and sharing information, reports, and perspective regarding our threat environment. We have…
Vehicle Ramming – a Threat to Faith-Based Organizations
By Sadie-Anne Jones On 08 June 2022, a man drove his vehicle into a group of students in Berlin, Germany. The attack resulted in the death of a teacher and the injury of 14 students. The incident happened close to…
FB-ISAO Threat Level, June 2022 Update
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The FB-ISAO Cyber Threat Intelligence, Operational Resilience (together, the Threat and Incident Response) working groups, have been actively monitoring and sharing information, reports, and perspective regarding our threat environment, to include…
FB-ISAO Threat Level Update – March 2022
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The FB-ISAO Cyber Threat Intelligence, Operational Resilience (together, the Threat and Incident Response) working groups, have been actively monitoring and sharing information, reports, and perspective regarding our threat environment, to include…
FB-ISAO Threat Level Update – Dec 2021
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The ongoing COVID-19 global pandemic is a complex and blended threat that impacts members and the broader faith-based and charity community in numerous ways. We have determined to maintain…
De-escalation Resources
Faith-based organizations often struggle to find a balance between securing their facilities and providing a welcoming environment for all those who walk through their doors. People gather at places of worship to do all sorts of things, to include worship,…
FB-ISAO Threat Level Update – Aug 2021
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The ongoing COVID-19 global pandemic is a complex and blended threat that impacts members and the broader faith-based and charity community in numerous ways. As of July 2021, we have…
FB-ISAO Threat Level Updates: Change to Physical Threat Level
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The ongoing COVID-19 global pandemic is a complex and blended threat that impacts members and the broader faith-based and charity community in numerous ways. As of July 2021, we have…
June 2021: FB-ISAO Threat Level Update
This message is TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. The ongoing COVID-19 global pandemic is a complex and blended threat that impacts members and the broader faith-based and charity community in numerous ways. For June 2021, we have determined…