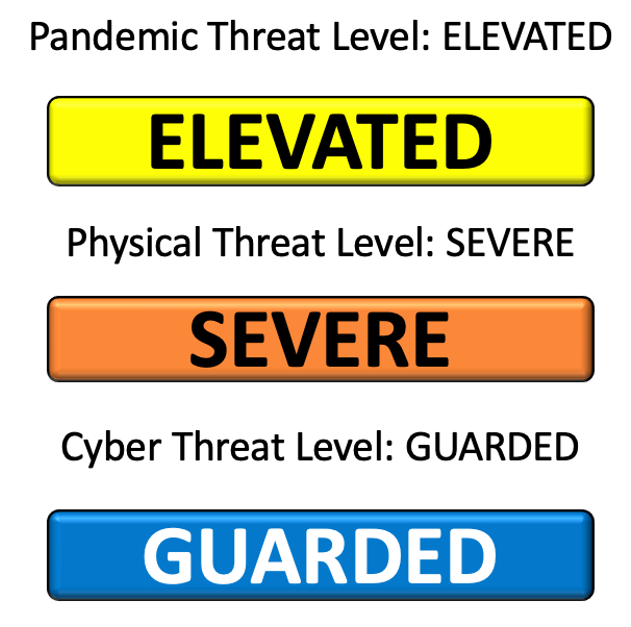
The TIG has determined to maintain the Physical Threat Level at “SEVERE.” SEVERE means an event is highly likely. The TIG will continue to assess the Physical Threat Level and provide updates accordingly. This determination is valid through sunset on 30 Sep 2020, and will be periodically re-evaluated, especially with respect to ongoing threats and developing federal, state, local, tribal, and territorial (FSLTT / SLTT) guidance and directives.
The TIG has determined to maintain the Cyber Threat Level at “GUARDED.” GUARDED means FB-ISAO is unaware of any specific or targeted cyber attacks, but a general risk of cyber attacks exist. The TIG will continue to assess the Cyber Threat Level and provide updates accordingly. Likewise, the cyber threat landscape will be continuously monitored, but this Cyber Threat Level determination is valid until further notice.