This DAP highlights First Baptist Church of Sutherland Springs: A Case Study on the Link Between Domestic Violence and Mass Attack, Wildfires Pose Growing Threat to Drinking Water Safety, and 2025 Hurricane Season Outlook: Not Quite 2024, But Above-Average US Landfall Threat. The DAP also has More Faith-Based Stories and Select All-Hazard Stories. These updates are shared to help raise the situational awareness of Faith-Based organizations to best defend against and mitigate the impacts from all-hazards threats including physical security, cybersecurity, and natural disasters.

The Cyber Road Show – An FB-ISAO Cyber Education Program
The Cyber Road Show is an entry-level opportunity for Faith-Based Organizations (FBOs) to gain a greater level of understanding relating to both general cyber security terms and threats and a specific cybersecurity threat, Business Email Compromise (BEC) and best practices.
To successfully conduct the Cyber Road Show, we worked with our Law Enforcement Partners in Virginia, Pennsylvania, Florida, Washington, DC, and New York (you can find a complete listing here.) We also assembled a team of Subject Matter Experts (SMEs) on the topic of Business Email Compromise.
During the 12 July Cyber Road Show, we discussed threat actor tactics, trends in BEC scams and mitigation strategies. Ronnie Tokazowski, Cyber Threat Intelligence Analyst at Cofense discussed how the number one cybercrime works. Participants in the FB-ISAO Cyber Road Show took a deep dive into BEC when they learned about the sophisticated scams targeting both businesses and individuals. BEC is frequently carried out when a threat actor posing as someone the target should trust—typically a colleague, boss or vendor. They then ask the target to make a wire transfer, divert payroll, or change banking details for future payments. There was a good deal of discussion on why BEC scams are difficult to detect! BEC attacks rely on impersonation and other techniques to trick people into interacting with them. BEC scams routinely begin with the hacking or spoofing of the email accounts in which they impersonate the role of a trusted person, i.e., chief executive officers or chief financial officers, and fraudulent emails are then sent requesting wire payments be sent to fraudulent locations (CEO Fraud). Over the years, the scam evolved to include compromise of personal emails, compromise of vendor emails, spoofed lawyer email accounts, W-2 fraud, romance scams, and fraudulent requests for large amounts of gift cards, as has been reported by FB-ISAO members where criminals have posed as rabbis and pastors reaching out to their congregations. And most recently for COVID scams.
Participants also learned that BEC scams are designed to use social engineering techniques and tactics which create a situation in which the target individual or company provides information of value to the attacker under perceived duress or pressure and without the targets of the scams being suspicious. In order to develop the appropriate scam, threat actors generally follow a series of steps.
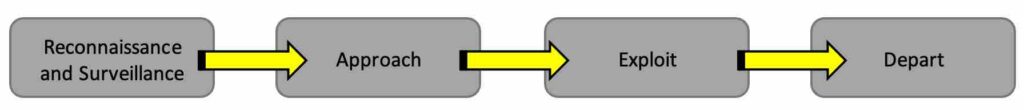
- Reconnaissance and Surveillance. The attacker will do their research to learn about the target, their weaknesses and to be able to select the right approach. This could begin with a simple phishing attempt to gain access to a network followed by days, weeks, months, or longer worth of to understand the target, their processes, and how they might respond to the approach.
- Approach. Using the knowledge gained, the attacker will deliver the scam to the target in an effort to provide legitimacy to their request while taking control of the situation with the target. The approach will be delivered to ensure there is an appropriate level of pressure applied to force the desired response.
- Exploit. Once the approach is accepted and access to the target is achieved, the attacker’s goal is to get in, get what they need and get out as quickly as possible. In some instances, this is expanding the breach and making lateral moves within the target to steal as much as possible, but also to enable future attacks. It is possible that the information gained from one attack can then be used in a follow-on attack against other targets.
- Depart. As much as possible, the goal in this phase is for the attacker to remove themselves from the scam without raising suspicion and calling attention to themselves.
Because FBOs are moving toward more online giving platforms and other online transactions, as well as engaging in third-party contracts for various services (Information Technology, custodial, or maintenance / construction projects), these BEC incidents can be just as common as in other industries. Threat actors could plan on their malicious request getting lost in the shuffle of a series of transactions or in a myriad of invoices. There are a couple of factors including not adhering to processes and procedures; poor security practices from individuals and organizations; the number of compromised accounts that are available on the dark web from any number of data breaches or leakages that are ripe for exploitation; and a continuously evolving threat.
Lastly, our panelists shared some red flags that employees need to be aware of that may signal a suspicious request:
- An unexplained urgency is communicated
- Last minute changes in wire instructions or recipient account information; or in established payment/communications platforms or email account addresses
- Communications only in email and refusal to communicate via telephone or online voice or video platforms
- Requests for advanced payment of services when not previously required
- Requests from employees to change direct deposit information
- URLs in emails are associated with the business it claims to be from
- Hyperlinks that may contain misspellings of the actual domain name
- The sender’s email address doesn’t match the purpose, or intent, of the communication (see image below)

To continue learning about Business Email Compromise and other scams, we assembled a resource page that can be accessed here. The FB-ISAO maintains a comprehensive list of resources for faith-based organizations to refer to for all their preparedness needs.
Members of FB-ISAO are encouraged to complete an Incident Report if they are victims of BEC, or if they experience any type of malicious incident. However, BEC-specific complaints can also be filed through the FBI’s IC3 at www.ic3.gov/Home/BEC. When available, each report submitted should include the date, time, location, type of activity, number of people, and type of equipment used for the activity, the name of the submitting company or organization, and a designated point of contact.
Programs like the FB-ISAO Cyber Road Show are delivered to the community of faith for free – yes free! The Cyber Road Show, and other programs like it, would not be possible without the generous support of our sponsors like Cyware Labs, AdvIntel, and Gate 15. If you, or your organizations would like to become a sponsor, please complete this form. Of course, donations are always welcome. FB-ISAO is 501(c)3, not for profit organization that provides members with information, analysis, and capabilities to help reduce risk while enhancing preparedness, security, and resilience. We are an all-faiths and all-hazards information sharing organization.



