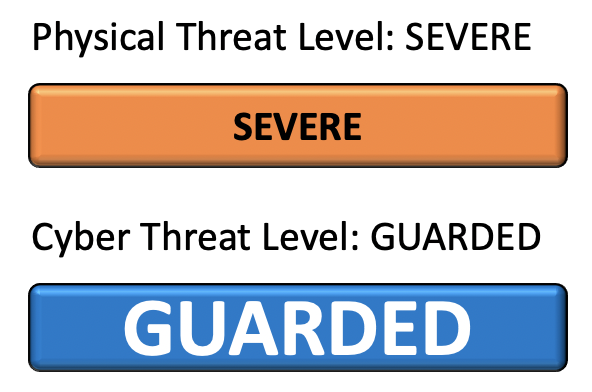
“If You See Something, Say Something®”
Resources for Faith-Based Organizations "If You See Something, Say Something™" is a national campaign that was developed and trademarked by the New York Metropolitan Transportation Authority (NYTA). The goal of the campaign is to minimize terrorist threats and increase public…