This DAP highlights – Ongoing Situation on U.S. Campuses. DAP also has More Faith-Based Stories and Select All-Hazard Stories. These updates are shared to help raise the situational awareness of Faith-Based organizations to best defend against and mitigate the impacts from all-hazards threats including physical security, cybersecurity, and natural disasters.

Hostile Events Attack Cycle – Intense Surveillance
by David Pounder and Brett Zupan
This post was originally informed by a TLP AMBER FB-ISAO Weekly Physical Security Report, distributed on 01 August 2019.
Special note: In light of the on-going hostile events and mass violence attacks, a Pittsburgh, PA parish cancelled a scheduled festival in response to a suspicious note.
On 13 August, a parish in Pittsburgh, PA painstakingly chose to cancel a scheduled festival that would have taken place 14-17 August. While no direct threat was made, the parish decided to cancel the festival out of an abundance of caution in response to a suspicious handwritten note received by the Diocese of Pittsburgh; the note said, “Cancel August 14-17 Festival Security Problem is Huge.”
FB-ISAO stresses the importance of considering all suspicious activity and treating threats seriously as leaders and organizations make threat-informed, risk-based decisions for their communities, as exemplified by the parish.
In our previous post in the Hostile Events Attack Cycle (HEAC) series, we reviewed the target selection phase of the HEAC. We highlighted three recent incidents (recapped below) to illustrate the process attackers go through when determining potential targets to wage attacks. Since that post was written, a recent arrest was made of a Las Vegas suspect with ties to a hate group accused of plotting to bomb synagogues and an LGBTQ bar.
- On 28 July, three people were killed when a shooter opened fire at the Gilroy Garlic Festival in Gilroy, California – the attacker’s reported target set was religious and political groups.
- On 3 August, a 21-year old killed 20 people and injured 26 more at a Walmart in El Paso, Texas – the attacker indicated his desire to “kill as many Mexicans as he could.”
In the early morning of 4 August, a 24-year old attacker killed nine people and another 26 were injured at the popular Oregon District in Dayton, Ohio – target set is inconclusive, but FBI reports the attacker had a history of violent obsessions and had mused about committing mass murder. - On 8 August, a 23-year old suspect was arrested in Las Vegas in connection with plans to surveil a Las Vegas bar he believed catered to LGBTQ clientele. An FBI-led task force found a notebook with “hand-drawn schematics” for a possible attack in the Las Vegas area. The suspect is identified as a registered security guard in Nevada. According to authorities, the suspect allegedly attempted to recruit a homeless person to conduct “pre-attack surveillance” on at least one Las Vegas synagogue and “other targets.”

As a quick review, target selection usually involves some symbolic value to the attacker, or motivation to gain publicity for a cause. The target selection process can occur consciously or subconsciously and is often influenced by a grievance and a sense of injustice, leading the attacker to feel the need to right the wrong. In this post, we explore how attackers build out their plan against their selected target by engaging in more detailed surveillance (intense surveillance) to increase the best chance of attack success.
Intense Surveillance
Once a target is selected, the attacker will resolve outstanding questions about the target environment, expand collection efforts through surveillance, and seek to adequately address remaining unknowns in order to ensure their attack is as successful as possible. While initial surveillance will help identify potential weaknesses within a target, the period of intense surveillance will go into much more detail and will involve a lot more “time on target” – time spent getting to know the target in-depth. Reports regarding the El Paso and Dayton attacks indicate the attackers spent time casing the areas before returning to their cars to arm themselves in preparation for the massacres. This intense surveillance allows the attacker to learn as much as possible and validate the initial attack plan. Likewise, it may even identify additional vulnerabilities that could make the target susceptible to a larger attack, or confirm alternate targets if the initial target is seen as too secure to permit an effective attack.
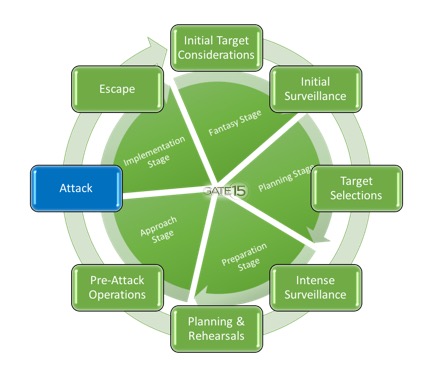
While all phases of the attack cycle are important, it could be argued that the intense surveillance phase can have the most impact in determining attack success or failure. This phase of the HEAC can take a long time. Depending on the target, some key questions intense surveillance will address include, but are certainly not limited to:
- What are the layers of security outside and inside the location; are there roving patrols on foot by security personnel or vehicle patrols; how often and how many people are involved?
- Does the facility have external surveillance platforms?
- Does the facility have a receptionist or check in area; what is that like?
- Are there alternate entrances that are not secure?
- Does the facility have a loading dock or delivery area; what is that security like?
- How often are deliveries made and on what schedule?
- What is the security response to suspicious events or materials?
In the Gilroy attack, it’s likely the attacker knew about the security processes in place at entrances, or at least knew there would be security to frustrate direct entry, but also understood the venue well enough to know that there would be access through the perimeter fence. Either way, research and surveillance conducted by the attacker allowed him to bypass security and exploit a gap. In the El Paso incident, the attacker was not from the area, but likely knew enough about these types of retail locations to inflict as much damage as possible prior to security response. Likewise, given that he surrendered to police, it is likely that he had anticipated how much time he had before police arrived.

It’s important to note, surveillance of a target does not always have to be done solely at the target site. Attackers can use similar type locations to identify potential vulnerabilities (and increasingly, attackers may conduct more and more of their targeting virtually). Recognizing similar venues will follow comparable protocols in their security plans, attackers can benefit from performing surveillance at other, like locations.
Know the Threat
As stated last time, all facilities, including places of worship, faith-based offices, other non-profits, and charities are potential targets for hostile attacks. The importance of maintaining awareness of the threat environment, potential threats to your organization(s), and an attack’s desired outcome is imperative – KNOW THE THREAT. FB-ISAO and its partners are dedicated to collecting and analyzing threat information to develop usable threat and risk intelligence to be disseminated/reported to the community of faith and to help organizations keep abreast of the current threat environment. Furthermore, through our ongoing work, resources, and Hostile Events Preparedness Series (HEPS) webinars, FB-ISAO aims to keep our members equipped to successfully prepare for and respond to any threat that should come against them.

David Pounder is Gate 15’s Director of Threat and Risk Analysis. He advises on both physical and cyber security issues. Dave spent over 20 years in the Army as an Intelligence and Security Officer, specializing in counter-terrorism, force protection, and counterintelligence efforts as well as serving in the private sector for leading financial institutions responsible for information security and mobile applications. Dave twice served in senior command positions responsible for both counterintelligence operations and investigations. He has briefed Senior Army Leadership on intelligence and security issues and operations to include General David Petraeus and General Martin Dempsey. David was a regular guest instructor at the Department of Defense Joint Counterintelligence Training Academy in Quantico, VA. Dave graduated from George Mason University and from the US Army’s Command and General Staff College and has served internationally to include tours in Iraq, Cuba and Qatar.

Brett Zupan is a Risk Analyst at Gate 15 with experience in all-hazards analysis, exercise development, and information sharing. He has supported analysis, preparedness and operations for a number of critical infrastructure communities, including support to Water and Wastewater Systems Sector, the Commercial Facilities Sector, and with Higher Education in support of REN-ISAC, among other projects. Before joining the company in 2016, he worked at the Georgia State Senate. Brett received his Masters of International Relations from American University.
Join FB-ISAO! We welcome faith-based organizations, charities and critical partners to join FB-ISAO. Access our TLP AMBER and TLP GREEN reports, join our collaborative forums, working groups, participate in leadership opportunities and take the next step in enhancing your organization’s preparedness, security and resilience!
- Donate to FB-ISAO today and help us execute our mission!
- Interested in sponsoring FB-ISAO, or our 2019-2020 FB-ISAO Workshop Series? Read more here and contact our team for more information!
- Learn about our Membership Programs
- Learn why your FBO, charity, or non-profit should join FB-ISAO
About our Vetting Policy
About the Traffic Light Protocol
Join today!



