by David Pounder and Brett Zupan
This post was originally informed by a TLP AMBER FB-ISAO Weekly Physical Security Report, distributed on 01 August 2019.
Over the span of two weekends, at least three hostile incidents serve as reminders of active shooter threats and ways in which they exploit vulnerabilities to wage attacks at open access venues, mass gathering places, and other public facilities.
- On 28 July, three people were killed when a shooter opened fire at the Gilroy Garlic Festival in Gilroy, California, approximately 20 miles south of San Jose. Within moments of the attack’s start, the suspect was quickly neutralized. While the festival did have wand and bag searches at the entrance, the attacker was able to cut out a portion of the fence on the perimeter of the festival along a creek. Additionally, the investigation revealed a list of targets that included religious and political groups.
- On 3 August, a 21 year old killed 20 people and injured 26 more at a Walmart in El Paso, Texas in an attack that began late in the morning. When officers arrived, the suspect surrendered without further incident.
- Finally, early in the morning of 4 August, an attacker killed nine people and another 26 were injured at the popular Oregon District in Dayton, Ohio, a historic neighborhood known for its nightclubs, bars, art galleries and shops.

These attacks highlight important considerations for faith-based organizations (FBOs). First, the Gilroy festival is a similar type of outdoor or community event FBOs often hold that attract people of all backgrounds. Many of these events may not have security, and even when security is present, attackers will likely seek ways to evade security measures. Second, the success of these attacks often give rise to copy-cat attacks in which potential or future attackers gain ideas to aid their plan or give them confidence they can be successful.
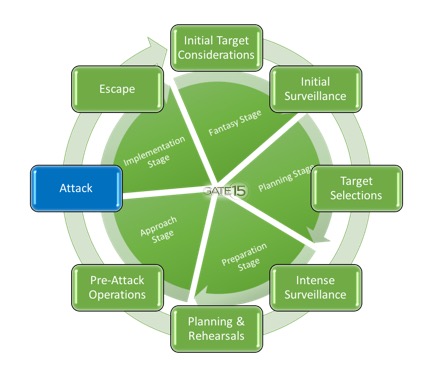
Acts of violence are rarely random. While attacks occur at any place and time, they tend to follow a predictable process identified as the Hostile Events Attack Cycle (HEAC). Whether an attack designed to inflict mass casualties and/or achieve global attention, or an attack on facilities or infrastructure, perpetrators go through an identified process (sometimes subconsciously) to plan, prepare, execute, and sometimes escape. Even seeming random acts of violence may incorporate parts of the HEAC, albeit usually abbreviated.
In this and future posts, we will explore the HEAC in greater detail, focusing on steps in the cycle, how the attacker conducts each step, and how organizations can prepare to defend against potential attacks. In this post we cover how attackers use initial planning to select targets.
Target Selection
Targets are often selected for symbolic value to the attacker, or to create the biggest media event to gain publicity for their cause. In the Gilroy attack, initial indications suggest the attacker had a grudge against certain types of people – people of color, mixed raced individuals, as well as Silicon Valley types – all of whom were likely to visit this festival. Similarly the El Paso attacker’s manifesto references his anger over the “Hispanic Invasion of Texas.” Reporting indicates the El Paso attacker did not have a specific target location in mind, and only after casing the Walmart minutes before the shooting determined it was suitable to “kill as many Mexicans as he could.” Regardless of motivation, results of the attacker’s steps through the remaining HEAC process largely determine the initial success of the attack.
The target selection process is based on a number of factors the attacker(s) work through consciously or subconsciously. Some factors include: stated goals, direction, or guidance of the core or central leaders (if the attack is part of a larger ideological effort,; i.e., international terrorist groups such as al-Qaeda or the Islamic State or organized white supremacist movements); resources and means available for attacker(s) to carry out the attack; security posture of the potential target; and desired effect or result of the attack. Target selection can also be influenced through grievances, as outlined in the recent FBI analysis, “A Study of the Pre-Attack Behaviors of Active Shooters in the United States Between 2000 and 2013.” “The cause of the active shooter’s distress or resentment – not necessarily based in reality – of having been wronged or treated unfairly or inappropriately.” The grievance leads to a sense of injustice and needing to right the wrong; it serves as the rationale for the attacker to carry out their attack, aids in target selection, and will push the attacker into the next HEAC phase (intense surveillance).
Know the Threat
All facilities, including places of worship, faith-based offices, non-profits, and charities are potential targets for hostile events. There are numerous direct and indirect threats to facilities daily. To understand whether your organization is a potential or specific target or may be in proximity to an event that could pose associated risks to your facility, it is important to maintain awareness of the threat environment, potential threats to your organization(s), and an attack’s desired outcome – KNOW THE THREAT.

Consuming threat and risk intelligence through information sharing organizations (including FB-ISAO), government partners, neighborhood hometown security partners, professional services, open source information, and other sources are important to ascertaining the threat level and potential attack scenarios to plan against. Adding to that understanding, familiarity with the stages and phases of the HEAC can also be very useful for defenders, as they reveal an attacker’s typical process. That familiarity can inform operation and preparedness activities and possibly help identify and disrupt a would-be attacker’s schemes. Through maintaining vigilance of surroundings, individuals can observe, identify, and report suspicious behavior or activity that could be a precursor to an attack. Recognizing how and when attacks against your organization may occur will enable security teams to develop informed risk assessments and develop sound protection strategies.

David Pounder is Gate 15’s Director of Threat and Risk Analysis. He advises on both physical and cyber security issues. Dave spent over 20 years in the Army as an Intelligence and Security Officer, specializing in counter-terrorism, force protection, and counterintelligence efforts as well as serving in the private sector for leading financial institutions responsible for information security and mobile applications. Dave twice served in senior command positions responsible for both counterintelligence operations and investigations. He has briefed Senior Army Leadership on intelligence and security issues and operations to include General David Petraeus and General Martin Dempsey. David was a regular guest instructor at the Department of Defense Joint Counterintelligence Training Academy in Quantico, VA. Dave graduated from George Mason University and from the US Army’s Command and General Staff College and has served internationally to include tours in Iraq, Cuba and Qatar.

Brett Zupan is a Risk Analyst at Gate 15 with experience in all-hazards analysis, exercise development, and information sharing. He has supported analysis, preparedness and operations for a number of critical infrastructure communities, including support to Water and Wastewater Systems Sector, the Commercial Facilities Sector, and with Higher Education in support of REN-ISAC, among other projects. Before joining the company in 2016, he worked at the Georgia State Senate. Brett received his Masters of International Relations from American University.
Join FB-ISAO! We welcome faith-based organizations, charities and critical partners to join FB-ISAO. Access our TLP AMBER and TLP GREEN reports, join our collaborative forums, working groups, participate in leadership opportunities and take the next step in enhancing your organization’s preparedness, security and resilience!
- Donate to FB-ISAO today and help us execute our mission!
- Interested in sponsoring FB-ISAO, or our 2019-2020 FB-ISAO Workshop Series? Read more here and contact our team for more information!
- Learn about our Membership Programs
- Learn why your FBO, charity, or non-profit should join FB-ISAO
About our Vetting Policy
About the Traffic Light Protocol
Join today!